Se você é fã dos caça-níqueis clássicos, simples e confiáveis, se você se lembra das máquinas caça-níqueis mecânicas e, pelo menos uma vez na vida, esteve em um cassino de verdade, isso significa que você provavelmente sente falta disso e não consegue relaxar totalmente e ficar satisfeito com os cassinos on-line.

Talvez tenha sido isso que os desenvolvedores da Booming Games pensaram e decidiram recriar essa atmosfera nostálgica no Burning Classics slot. E, olhando para frente, posso dizer que eles foram bem-sucedidos.
Burning Classics: jogo quente com símbolos clássicos
A Burning Classics é uma verdadeira slot clássica, construída no esquema 5-3. Ela tem todas as mesmas coisas que você veria nos caça-níqueis mecânicos dos cassinos de Las Vegas: cerejas, setes, limões, além de grandes vitórias.
Ao mesmo tempo, tudo isso é realizado com a tecnologia moderna e os artifícios dos caça-níqueis on-line. Além do alto nível de detalhes de todos os elementos, o Burning Classics slot deixa claro que o jogador está lidando com um jogo sério.
Talvez por tudo isso, o Burning Classics slot seja muito popular entre os jogadores de todo o mundo. Os jogadores brasileiros, que também gostaram da nostalgia com um toque de alta tecnologia. No Brasil, o jogo está disponível em plataformas comprovadas:
- Pin-UP
- Monro
- BC.GAME
Tenha cuidado ao escolher um cassino e sempre verifique as informações que estão disponíveis para os jogadores nos sites de cassino. Isso o ajudará a evitar fraudes e o vazamento de seus dados pessoais.
A Magia dos Símbolos Clássicos
Todos os caça-níqueis clássicos utilizam símbolos na forma do número 7, limão, cereja, sino e similares. O Burning Classics slot segue essa tendência e usa símbolos semelhantes em seu campo de jogo, embora em uma versão digital.
Para começar a jogar, você faz uma aposta e gira os rolos. Para obter uma combinação vencedora, é necessário coletar três ou mais símbolos em uma linha. Entretanto, diferentemente dos caça-níqueis clássicos, o Burning Classics slot oferece aos jogadores a opção de obter uma das 20 linhas de pagamento possíveis. Isso significa que será mais fácil para você ganhar, pois poderá obter a combinação necessária na vertical, horizontal ou diagonal.
O tamanho das apostas varia de 0,2 a 200 unidades monetárias, o que é um tipo de padrão no mundo do cassino virtual. E os pagamentos, dependendo das combinações caídas e do valor de determinados símbolos do jogo, você pode estudar em detalhes na tabela abaixo. Observe que não há nenhum símbolo BAR nesse jogo e não está muito claro para mim por que os desenvolvedores não o adicionaram.
| Símbolo | Índice de pagamento |
| Sevens (todas as cores) | 2:1 |
| Ameixa, cereja | 0,5:1 |
| Melancia, limão | 1:1 |
| Wild | 10:1 |
| Free Spins | 400:1 |
Observe que a tabela mostra os pagamentos máximos. A propósito, sua sorte pode lhe dar a oportunidade de ganhar o jackpot, que para o Burning Classics slot será 2.000 vezes a sua aposta inicial – sólido, certo?
Recursos Especiais para Aquecer o Jogo:
Como muitas outras máquinas caça-níqueis, a Burning Classics slot tem vários símbolos e recursos especiais. Entre eles, o Wild e as Rodadas Grátis oferecem uma vantagem especial.
O Wild, como em outros caça-níqueis, dá a oportunidade de substituir qualquer símbolo desfavorável no campo de jogo, se ele impedir a criação de uma combinação vencedora. Além disso, vários Wilds reunidos em uma combinação (mínimo de 3) lhe trarão um pagamento sólido, que pode ser 10 vezes a sua aposta.
O símbolo de Giros Grátis também tem um duplo significado. Por um lado, coletar um mínimo de 3 desses símbolos abrirá uma rodada de bônus na qual você ganhará várias rodadas grátis (máximo de 20 por rodada). Por outro lado, o mesmo símbolo pode lhe dar, aleatoriamente, a oportunidade de ganhar 2.000 vezes a sua aposta inicial – para isso, você precisa coletar uma combinação de 5 símbolos de Rodadas Grátis. As chances são mínimas, mas existe a possibilidade de tal resultado.
Rodadas Grátis: Embarque em uma Aventura Premiada:
É importante perceber que são os sinais de Giros Grátis que têm um valor especial para os jogadores, pois eles fornecem a maneira mais fácil de passar para a rodada de bônus com giros grátis e multiplicadores aumentados no campo de jogo.
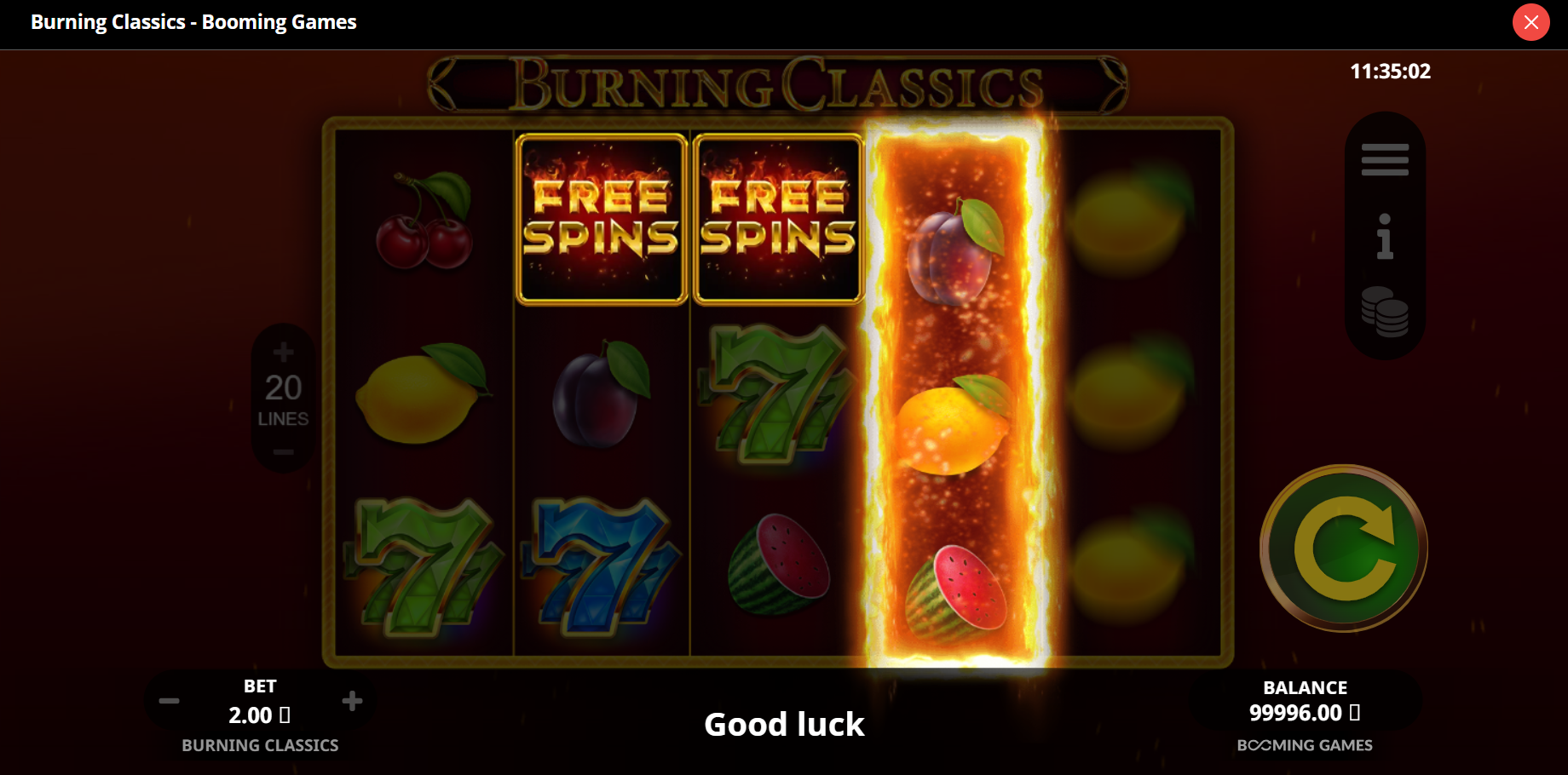
Ao coletar uma combinação de 3, 4 ou 5 sinais especiais, o jogador receberá 10, 15 ou 20 rodadas grátis. As rodadas grátis também podem ser obtidas por meio de uma compra durante o jogo ou ao se registrar como um novo usuário no site do cassino. No entanto, é muito mais interessante obtê-las diretamente durante o jogo, por seus próprios esforços, em vez de por meio de compra ou registro.
As rodadas de bônus com Giros Grátis estão disponíveis durante toda a sessão e não são limitadas a uma única vez. Teoricamente, elas podem ser ativadas um número infinito de vezes, mas quero lembrá-lo de jogar com responsabilidade e com intervalos.
Além disso, durante a rodada de bônus, as figuras no campo de jogo multiplicam seus valores várias vezes, o que aumenta seus ganhos potenciais. E não se esqueça do jackpot: você pode ser o ganhador do prêmio.
RTP e Volatilidade: Encontre o Seu Estilo de Jogo
O RTP do Burning Classics slot é de cerca de 96% – essa é a média das máquinas caça-níqueis, mas certamente não é a menor. No entanto, esses valores significam que, no final da sessão de jogo, você pode retornar cerca de 96% do seu saldo inicial (é claro que tudo isso é teórico e você precisa ser esperto em relação às suas apostas e ao seu saldo).
Além disso, esses valores de RTP também significam que os multiplicadores de bônus (incluindo os recordes) ocorrerão claramente na Burning Classics slot.
Quanto à volatilidade, aqui ela está em um nível médio. Isso significa que o risco de perda existe, mas não é o mais alto. Ao mesmo tempo, a chance de roubar o prêmio também diminui, pois esses dois indicadores estão inter-relacionados. De qualquer forma, a distribuição competente das apostas e a capacidade de parar a tempo desempenham um papel muito mais importante no caça-níquel do que os indicadores teóricos.
Mesmo se você comparar o RTP e a volatilidade do Burning Classics com outros caça-níqueis populares no Brasil, ficará claro que esse caça-níquel, se não for superior, pelo menos está no mesmo nível dos outros.
| Indicador | Burning Classics | Gates of Olympus | Crazy Monkey |
| RTP | 96% | 96% | 96% |
| Volatilidade | Médio | Médio | Médio |
Jogue Grátis e por Dinheiro Real
Se você está em dúvida se deve jogar no Burning Classics slot, tenho boas notícias para você: você pode experimentar toda a mecânica na versão de demonstração gratuita. É basicamente o mesmo jogo, mas você não precisa apostar dinheiro de verdade (nem ganhar prêmios).
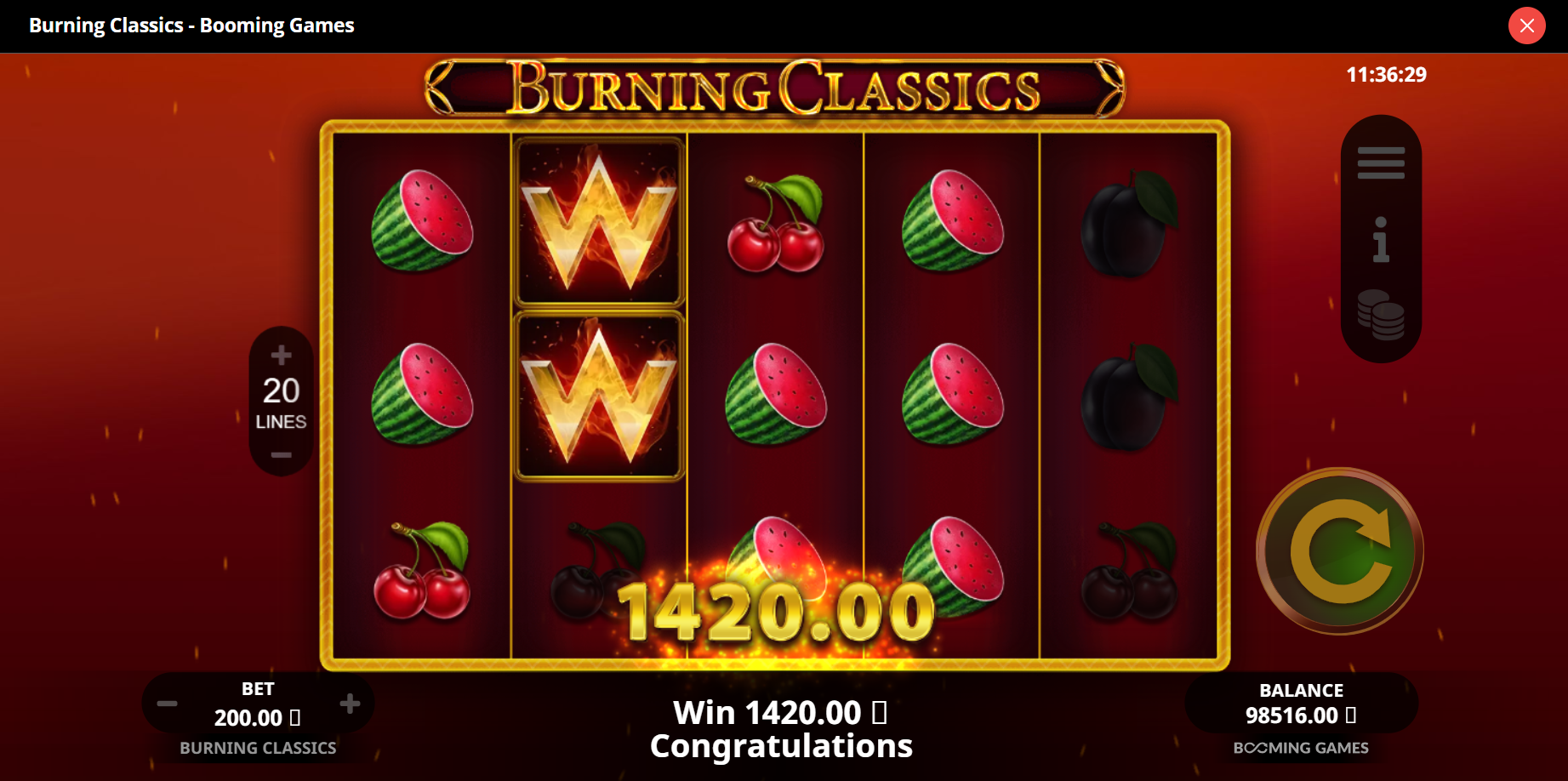
Essa é uma ótima oportunidade para experimentar toda a mecânica do jogo, acostumar-se com o visual, aprender as combinações e o significado dos símbolos. Além disso, você poderá entender se está interessado no Burning Classics slot ou se não é fã desse tipo de caça-níqueis e prefere jogos mais modernos (em todos os sentidos).
Quando estiver interessado e pronto para começar a jogar com dinheiro real, escolha um cassino e comece a ganhar. Quero chamar sua atenção para o fato de que, antes de mais nada, é preciso escolher um cassino para jogar (a lista dos mais populares está nesta análise). Registre-se, receba generosos bônus de boas-vindas na forma de rodadas grátis e bônus para o seu depósito, procure o Burning Classics slot e comece a ganhar!
Mas o mais importante: jogue com responsabilidade. Certifique-se de estabelecer limites para não perder tudo de uma vez, fique de olho em sua relação de ganhos/perdas e faça intervalos entre as sessões de jogo. Isso o ajudará a evitar o vício em jogos de azar, mas não hesite em procurar ajuda externa também. No Brasil, a ajuda mais qualificada para o vício em jogos de azar é fornecida pela Terapia do Jogo – lembre-se, por via das dúvidas.
Conclusão: Um Clássico Moderno para Jogadores Brasileiros
De fato, o Burning Classics slot acabou sendo incrivelmente empolgante. O provedor conseguiu combinar com sucesso o estilo visual clássico inerente às máquinas caça-níqueis com gráficos de alta tecnologia e mecânica de jogo. O resultado é um excelente produto que será interessante tanto para iniciantes quanto para jogadores experientes que sentem falta dos clássicos.
O caça-níqueis Burning Classics é extremamente rápido de dominar para todas as categorias de jogadores, com um modo de demonstração gratuito para você experimentar toda a mecânica.
Fiquei satisfeito com os belos gráficos, bem como com o alto potencial de ganhos desse caça-níquel. E tenho certeza de que você também gostará do Burning Classics.
